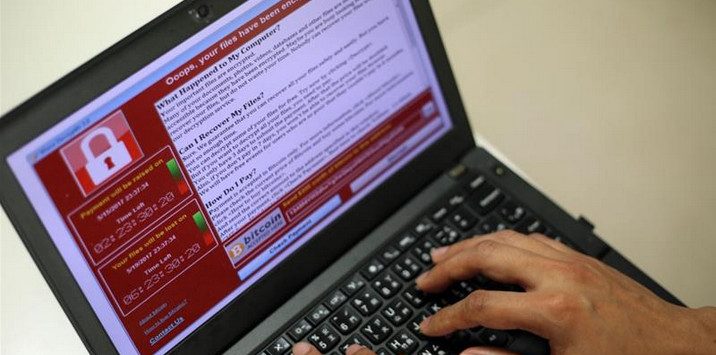
Beginning May 12, nearly 300,000 computers in more than 150 countries fell victim to the WannaCry ransomware attack. In Great Britain, the attack paralyzed network systems of multiple hospitals, resulting in suspension of some surgical operations. In China, the foremost victims were campus networks at institutions of higher learning, with a number of college graduates finding their theses destroyed. The attack did not subside until three days later. Most of the damage proved irreparable.
The attack may have resulted in greater losses. It took advantage of the EternalBlue loophole in the Windows operating system, in combination with advanced Trojan and backdoor tools. Some of those tools came from the cyberweapons arsenal of the US National Security Agency. And the militarized means of attack were originally intended for paralyzing a country’s network facilities. Fortunately, the international community responded unusually rapidly to the attack. Several major internet service providers, including 360, Tencent and Baidu, came up with patches targeted at WannaCry at the first instant; the Chinese and US network emergency response centers immediately issued warnings; Microsoft offered upgrade services for the Windows XP system, for which it had stopped services. With the concerted efforts of national governments and enterprises, spread of the attack was curtailed quickly. There has been no second-wave attack.
Following WannaCry, similar attacks have not stopped, hackers are developing more advanced tools. A similar, or even more damaging internet disaster may occur at any moment. However, the incident has also offered some valuable inspirations for the international community, and clarified some misgivings about international cyber cooperation, which will also benefit China-US collaboration on cybersecurity.
First, no country can survive a global internet disaster. WannaCry showed a form of attack that has been rare in recent years. The attacker has no certain, clear target. Instead, the perpetrator tried to infinitely expand the scope of the ransomeware’s dissemination, targeting every internet user. Spread of the ransomeware was so fast that it surpassed the attacks by LoveLetter and Worm.WhBoy.cw. This attack showed hackers’ internet attack techniques have seen conspicuous progress, demonstrating the capacity for breaking through countries’ current cybersecurity systems and doing damage on a large scale. Therefore, there is no “zero-sum game” or “absolute safe area” in cyberspace. It is thus impossible for individual countries to meet this kind of challenge via enhancing their own cybersecurity capabilities. The only viable defense is broader international cooperation.
Second, militarization of the internet has worsened uncertainties and the sense of insecurity in global cyberspace. Over the years, major Western countries, with the US leading the way, have actively sought to enhance military capabilities in cyberspace, setting up cyber forces and developing cyberweapons. The tools employed in this attack originated from US-developed cyberweapons. The US believes cyberweapons are an important part of US military strength, and can be used in such fields as antiterrorism and non-traditional warfare, and constitute deterrence against potential rivals. But it has yet to realize that unlike traditonal weapons such as aircraft carriers, aircraft and artillery, cyberweapons are more like makeshift firearms or explosives, which can easily get lost or proliferate, and criminal elements can easily remake or refit them when necessary. Under such circumstance, the risk of cybermilitarization has been considerably under-estimated, and other countries’ cyberweapons, too, can be acquired by hackers or terrorists.
Third, information-sharing is the most effective, most direct ways to reduce cybersecurity threats. That national governments and companies quickly came up with tailored patch programs was a main reason that the spread of WannaCry was immediately subdued. Technically, program developers can’t avoid loopholes in system or software products, some loopholes may be identified years later and exploited by hackers. Under such conditions, national governments and companies are obliged to share information about identified loopholes, rather than profiting from the holes or using them to develop cyberweapons. The Chinese Law on Cybersecurity, passed on June 1, includes many stipulations on system loopholes, requires companies to timely report and address system loophoes they detect, and promises severe crackdown on cybercrimes that abuse system loopholes. The US government and companies should understand the intention and purpose of this law. Considering the grim conditions of cybersecurity, China needs a complete, comprehensive set of legislations to contain cybercrimes and inappropriate conducts, improve corporate cybersecurity awareness, and upgrade capabilities of self-protection in cyberspace. As indicated by the simultaneous emergency responses of Chinese and US companies, the two countries’ stances are consistent at this point.
Such inspirations offered some viable routes for China-US cybersecurity cooperation in the next stage. For example, China and the US should further enhance information-sharing about transnational hacker organizations and joint law-enforcement so as to deal with the sources of such threats. They should enter early-stage cooperation on arms control in cyberspace and prevention of cyberweapons proliferation, prevent cyberweapons from being acquired by hacker organizations, and restrain the cyberweapons’ damaging potentials against civilian facilities. The two should also further strengthen cooperation on cyberthreat information sharing, especially give full play to the technological advantages of each country’s enterprises in such collaboration, so as to reduce mutual suspicion and misunderstading.
China US Focus

